
Algorand Sustainability Proposal: Backrunning MEV
This is presented as a personal opinion piece. Views presented here are mine except where explicitly attributed. Preface In conversations about sustainability and fees on Algorand, most of the focus so far has been on: raising the minimum fees, or changing the supply model to inflate/deflate dynamically with usage and to a lesser extent: priority fee ordering - higher fee gets earlier placement in block I propose an alternative protocol change in the broader “priority fee” market. This is a personal proposal, presented here as my recommendation to the community for discussion. ...

Algorand Sustainability Proposal: Excess Transaction Fee Rebate
This is presented as a personal opinion piece. Views presented here are mine except when explicitly attributed. Algorand fee sustainability has recently come back into the community spotlight. In this debate, there is considerable traction behind the notion that increasing the minimum transaction fee will negatively impact adoption: high volume applications may reduce their on-chain volume (or stop altogether) and certain use cases - micropayments or microinteractions - may no longer be viable on Algorand. ...

Dear Ora: A signable open letter to Ora miners
TL;DR at bottom Preface Let me preface this by stating my own opinion about, and relationship with, Ora. I like Ora. I use Ora. I can even claim to being a kind of Godfather to it, having “given” it asset ID 1284444444. In light of the first Ora halving, I took a look at Ora statistics and mining practices. My objective here is to make a recommendation on Ora mining practices to reduce Ora’s negative externalities on Algorand infrastructure, while at the same time appreciating the positive externalities. ...

Thoughts on "a" musing on the pond: Dynamic supply for Algorand
The “Musings on the pond” article lays out a thought-provoking proposal for a deep intervention in Algorand’s economics. If you have not read it, it is well worth putting it at the top of your reading list and getting to it soon - even now, in fact: if you have the time, go read that first. Among the proposed interventions is a set of changes to the minimum transaction fee, block rewards and fee burns that would alter the fixed nature of the total supply of Algorand. The present article discusses these changes. ...

Disclosure Tales 02: Downward Facing DAOs
I discovered and disclosed a vulnerability in the Updog and FAME DAO contracts. Then I hacked them. This story is not boring. Background: The DAOs Updog offered a fully featured DAO platform. In a nutshell: Each DAO instance has a governance token that can be staked and withdrawn. The DAO contracts could control assets and ALGO. Payments of both types could be executed trustlessly after a proposal passed with enough votes. Voting power is proportional to the staked amount of governance tokens in the DAO. ...

Disclosure Tales 01: Honing Fire
I discovered and disclosed a vulnerability in the Hone NFT shuffle contracts. They responded well. This story is almost boring. The backstory I was curious about the mechanics of the Hone NFT shuffle, as it utilizes VRF, in which I have a keen interest. Reading TEAL is a bit like reading assembly, but with enough determination and a bit of practice you can figure out what a contract is doing. Occasionally you can also spot a combination of transactions or parameters that breaks the assumptions of the contract developer. The dopamine rush from finding and verifying a vulnerability in a smart contract is probably equivalent to snorting 1,000 ground-up sudoku puzzles. ...

Set Up Voi Participation Node on Ubuntu 22.04
This article will guide you through setting up a Voi participation node on the latest Ubuntu LTS (22.04). It assumes you start with a local or remote (server/cloud) installation. Version 20.04 should also work, but is not tested extensively. This guide is only suitable for x86 architecture machines as it relies on the Algorand repository, which does not publish packages for other architectures such as ARM64. ⚠️ Do not follow this guide if you are running an existing Algorand node on the same server, at it will likely overwrite your Algorand installation. 🪙 You will need to have some $VOI balance to complete this guide. You will need $VOI because: ...

Implementing an on-chain VRF shuffle for EXA Lootbox Reveals
Following a brief partnership during CupStakes - where EXA.market was our official secondary marketplace - they commissioned me to implement the smart contracts that would power their rewards program. As a new marketplace in the Algorand ecosystem, EXA wanted to incentivize users to trade on their platform. Users were rewarded with “Lootbox” NFTs for using the platform. After the lootboxes were distributed, we revealed that there were two more kinds of lootbox users could get. By merging 3 of their original (level 1) lootboxes they could get a level 2 lootbox, and by merging 3 of their level 2 lootboxes they would get a level 3 lootbox. This “merge” was performed by the first smart contract I developed for EXA. ...
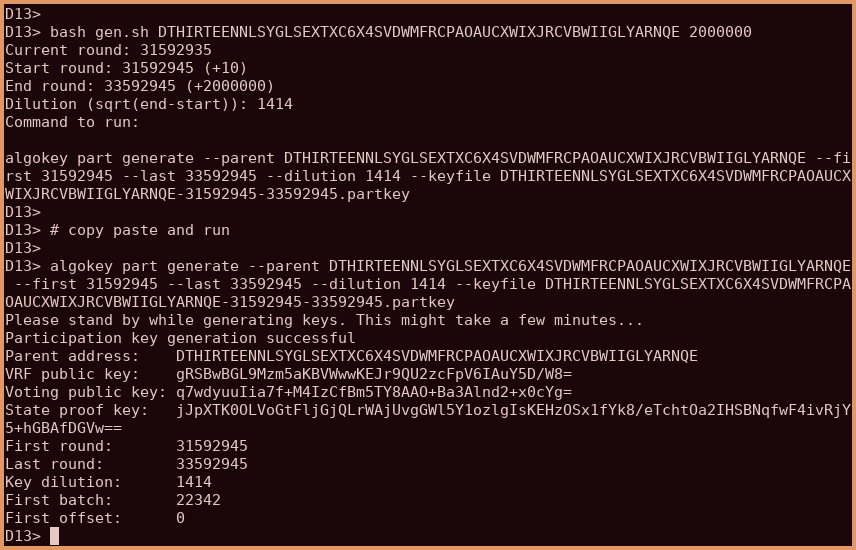
Redundant Participation Nodes on Algorand
⚠️ Article content under review. Check back later.
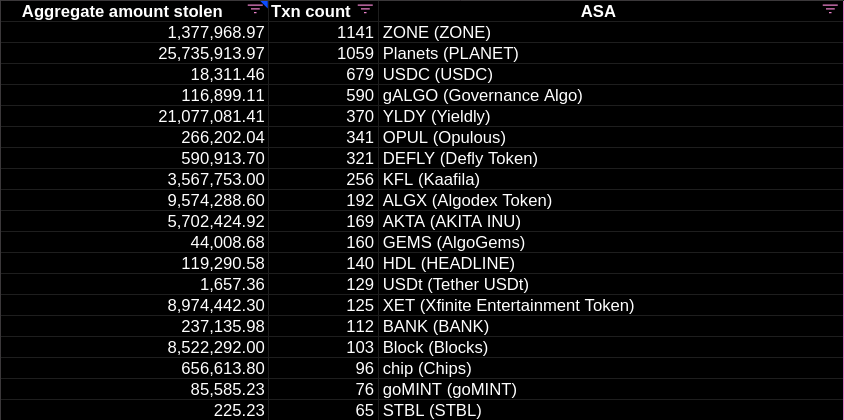
MyAlgo hack: Fifth Wave - Addresses & Data
The MyAlgo attacks have so far been clustered around five distinct waves, roughly corresponding to these dates: First Wave: February 20, 2023 Second Wave: March 5, 2023 Third Wave: March 6, 2023 Fourth Wave: March 17, 2023 Fifth Wave: March 31, 2023 This article presents data from the fifth wave - March 31 - as well as subsequent movements of stolen funds. Summary The attack was automated and ran for 14 hours - from 2023-03-31 10:15 (GMT) until 2023-04-01 00:25 (GMT). ASAs were drained from 4,166 accounts into the following malicious account: ...